Block malicious scripts from running on your computer
Back in the salad days of early summer, JavaScript was usually employed to download ransomware payloads. Now, however, JavaScript is the ransomware.
The reason is the direct nature of the attack. There’s no connection to a suspicious subdomain, no payload to download and no relying on the user to run a suspicious “upgrade“ to a Windows component.
Simply open the email attachment promising unexpected riches and, to misquote the 1980s game Zero Wing, “All your file are belong to us“.
Block malicious scripts
By hiding the true nature of the file with a second, benign extension, JavaScript attachment attacks become even more likely to detonate. Spew millions of such emails from a rented botnet for a few days at a time, and then simply wait for the Bitcoins to come rolling in.
It’s little wonder that ransomware gangs are setting up customer helplines for bemused punters queuing up to get their files back.
It’s little wonder that ransomware gangs are setting up customer helplines for bemused punters queuing up to get their files back.
But surely your browser’s sandbox should contain any malicious JavaScript? Sadly, this is not so for JavaScript email attachments. JavaScript downloaded as part of a browsed web page is run in the browser. Email attachments are nothing to do with a web page. Double click them and they’re passed to the Windows Based Script Host, which is obviously outside the browser’s authority and control.
Open with a safe app
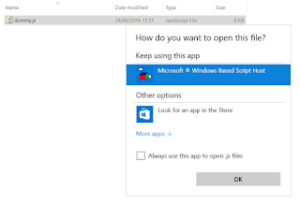
It is, however, very simple for you as an end user to stop JavaScript email attachments from automatically being accidentally run. Simply open notepad and create a new file. Save it as dummy.js. Notepad will complain about the extension, but continue anyway. Next, right click the .js file and select “Open With…“. As you can see from the image below, by default Windows will open all such files with Windows Based Script Host, which is what we need to prevent.
To do so, first click “More Apps“ and select Notepad from the list. Tick the check box for “Always use this app to open .js files“ and click OK. Now, whenever you absent-mindedly click on a JavaScript email attachment it will safely open in Notepad and display its bad self.
You can also selectively prevent the JavaScript downloaded as part of a web page from running in your browser. This gives you more control over your browsing experience and can speed up web page loading.
For Firefox, the go-to solution here is the NoScript plugin (which is the one I’m most familiar with). By default, NoScript blocks everything on a domain-by-domain basis. It’s easy and quick to unblock trusted domains as you go, while leaving all others (including those called by the primary domain) securely blocked. This not only serves as an extra line of defence, but also prevents some adverts from being displayed without sites accusing you of using an ad blocker. It’s also very interesting, and sometimes worrying, to see just how many secondary domains some of your favourite web sites rely on to deliver content.
 All posts
All posts